An unprecedented phishing attack targetting clients of major banks has been discovered in Vietnam. The campaign impersonates 27 popular financial institutions and remains active at the time of writing.
The cybercriminals seek to reap highly detailed personal information from the clients of those institutions to the extent of robbing their bank accounts, using techniques that allow them to bypass OTP verification.
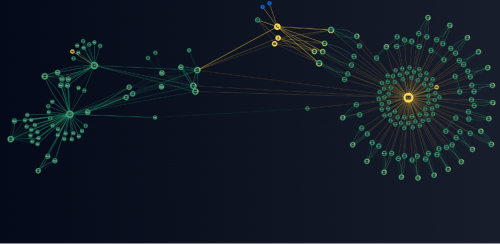
Group-IB, a cybersecurity company headquartered in Singapore, said its Computer Emergency Response Team (CERT-GIB) has identified 240 interconnected domains that are a part of the phishing campaign’s infrastructure.
“Upon detection of this activity, CERT-GIB immediately notified Vietnam’s national computer emergency response team VNCERT. All 240 domains have been blocked following CERT-GIB and local authorities’ efforts. Yet, new domains regularly appear,” the cybersecurity firm said in a statement.
This phishing campaign was initially launched in May 2019, when the first domain was registered. The latest phishing domain was activated on 1 June 2022.
CERT-GIB notes that this is by design as the domains are intended to only be active for short periods of time, which complicates detection and takedown. For this reason, too, the actual number of domains could be significantly higher.
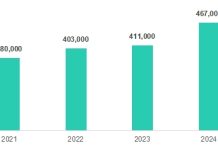
CERT-GIB was able to retrieve the number of visitors to 44 out of 240 websites identified, where web counters were installed. Just since the beginning of 2021, at least 7,800 potential victims visited these 44 phishing resources.
The overall number of visitors and affected users is unknown but is believed to be significantly higher, taking into account the scale, duration of the fraudulent operations and the degree of sophistication in the methods used by the cybercriminals.
‘Swiss army knife’ phishing
The phishing scheme leverages rogue SMS, Telegram and WhatsApp messages, and even comments on Facebook pages of legitimate Vietnamese financial service companies to lure victims to their phishing pages.
One of the scammers’ SMS, retrieved by CERT-GIB, informed the victim that they have been awarded a gift and needed to login to their banking portal to claim it. Upon clicking on such links, the victims are forwarded to a fake web page featuring the logos of 27 highly reputed banks and financial institutes either as a single page or as a drop-down option for victims to pick their registered bank.
Then, they will be redirected to another phishing page disguised as a legitimate banking portal. Should the victim input their username and password, they are taken to the next fake web page where a One Time Password (OTP) is requested. At this point, the fraudsters use the already stolen credentials to login into the victim’s real account.
After the victim submits the OTP to the fake authentication page, the cybercriminals will gain full access to his/her bank account and be able to initiate unauthorised illicit transactions.
Then, once the victim logs in to the fake account, they are presented with a message that says that “the transaction is still processing”.
To date, Group IB noted that the campaign appears restricted to Vietnam. “CERT-GIB continues to monitor the infrastructure for new domains and phishing tactics. In the meantime, users should note that communications from their financial institutions that seek to create a sense of urgency or intimidation are red flags,” it said.
It’s important to pay attention to the domain name of the URL in the browser and be wary of websites that appear to malfunction or create long chains of redirection. Users should avoid purchasing from unauthorised resellers or clicking on links that offer discounts. They are likely fraudulent.
“Also, it is critically important to confirm the credibility of the source. Enabling two-factor authentication wherever possible and changing passwords from time to time are also good habits,” said Group-IB.