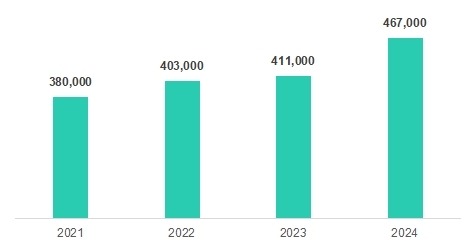
In 2024, Kaspersky’s detection algorithms found 467,000 harmful files on average per day, a 14% rise over the year before. Experts reported a 33% increase in Trojan detections compared to 2023, indicating a notable increase in several threats.
The Kaspersky Security Bulletin (KSB), an annual series of publications examining significant advancements in the cybersecurity landscape, describes these and other discoveries.
With Windows generating 93% of all malware-infected data found every day, it remained the most popular target for assaults. Among the top three threats, malware families spread by different scripts and MS Office document formats accounted for 6% of all dangerous files found every day.
The Kaspersky security products found an average daily count of harmful files between January 1st and October 31st, 2021–2024.Between 2023 and 2024, Kaspersky’s detection technologies found a notable 19% growth in Windows malware.
With a 33% increase from 2023 to 2024, Trojan horses—malicious programs that pose as trustworthy software—remain the most prevalent kind of malware.
The use of Trojan droppers, which are programs intended to infect a victim’s computer or phone with further malware without the user realising it, has also increased by a factor of 2.5 (150%).
As adversaries continue to create new software, tactics, and methods to target individuals and organisations, the number of new threats increases annually. This year was no exception, and risky patterns were noted, including assaults on supply chains and reliable connections, including those on open-source software (e.g., the XZ case).
There was a notable surge in banking malware, as well as widespread phishing and criminal activities targeting social media users. Of course, AI technologies are also being used to aid in phishing attacks and create new viruses.
In the ever-changing world of cyber threats, using trustworthy security solutions is essential. Vladimir Kuskov, head of anti-malware research at Kaspersky, said, “Kaspersky experts are always committed to countering new and challenging cyberthreats, ensuring a secure online experience for users as well as robust cybersecurity and the latest threat intelligence for organizations.”
The Kaspersky Security Bulletin (KSB), an annual compilation of forecasts and analytical studies on significant developments in the field of cybersecurity, includes these findings, which are based on Kaspersky’s malicious file detections from January to October.
- The following advice can help you stay safe:
Individual users: Avoid downloading and installing programs from unreliable sources. Avoid clicking on links from dubious websites or dubious internet ads. Whenever possible, use two-factor authentication. Use a combination of capital and lowercase characters, digits, and punctuation to create secure and distinctive passwords.
To assist with password recall, use a trustworthy password manager. Install updates as soon as they become available, as they address significant security flaws.Use a strong security solution suitable for your system type and devices, like Kaspersky Premium, and disregard notifications requesting that you disable cybersecurity or office software security measures.
Institutions: Maintain software updates on all of your devices to stop hackers from taking advantage of security holes to enter your network. Always use strong passwords for remote desktop services (like RDP) and only expose them to public networks when absolutely required.
Utilise programs like Kaspersky NEXT EDR Expert to gain complete visibility across all endpoints on a business’s corporate network, automate repetitive EDR operations, and empower analysts to quickly identify, rank, look into, and eliminate sophisticated threats and APT-type assaults.
Use the most recent threat intelligence data to be informed about the real TTPs that threat actors employ. Make frequent backups of the company’s data. Network isolation is necessary for backups. Ensure that you can easily retrieve the backups in case of an emergency.