Singapore-based Cybersecurity Firm Reveals Automated Telegram-Based Phishing Scheme Targeting 251 Brands Across 79 Countries
Group-IB, a renowned global cybersecurity firm headquartered in Singapore, has unveiled the relentless expansion of Classiscam, a scam-as-a-service operation, well into 2023.
In a newly released blog post, Group-IB analysts delve into the intricate workings of this automated scheme, highlighting its utilisation of Telegram bots to facilitate the creation of ready-to-use phishing pages that impersonate companies across various sectors, including online marketplaces, classified sites, and logistics operators. These deceptive pages are meticulously designed to siphon money, payment data, and, in recent instances, bank login credentials from unsuspecting internet users.
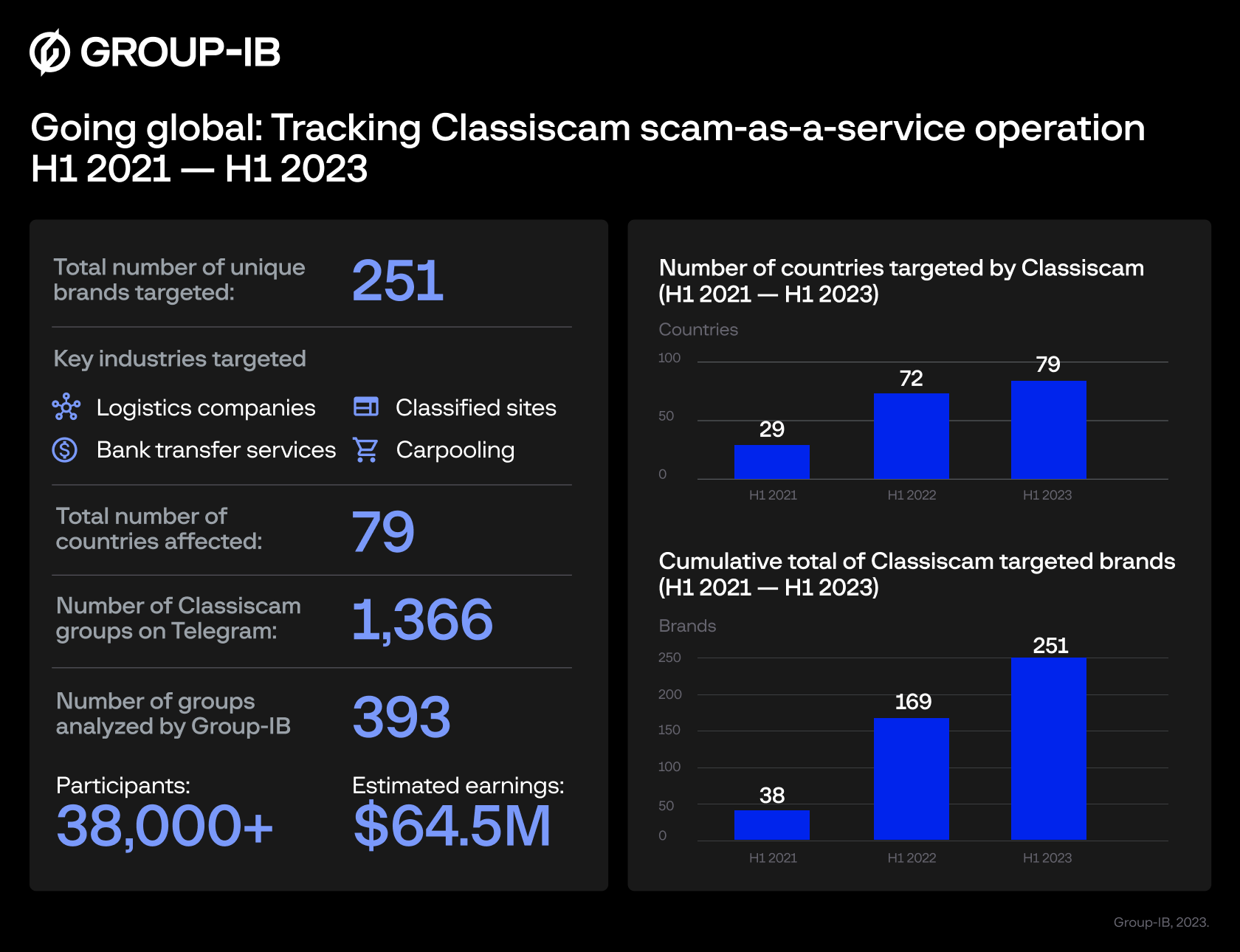
Group-IB’s research has unveiled a staggering 251 unique brands from 79 countries featured on Classiscam’s phishing pages between 1H21 and 1H23. Moreover, these phishing templates can be localized for different countries by adjusting language and currency settings, resulting in one logistics brand being impersonated across as many as 31 countries.
Within the Asia-Pacific (APAC) region, Australia emerged as the most heavily targeted country by Classiscammers, accounting for 34.6% of the regional total. Other significantly affected countries include India (11.5%), Hong Kong (10.3%), Singapore (7.7%), Sri Lanka (7.7%), and Malaysia (5.1%).
Since the latter half of 2019, when Group-IB’s Computer Emergency Response Team (CERT-GIB) collaborated with the Digital Risk Protection unit to identify Classiscam’s operations, they have discovered 1,366 distinct groups employing this scheme on Telegram.
Further investigation has focused on 393 Classiscam groups, encompassing over 38,000 members, operating between H1 2020 and H1 2023, collectively amassing an estimated US$64.5 million in earnings. Notably, Classiscammers have continuously evolved their tactics, introducing innovations such as phishing schemes aimed at pilfering victims’ online bank account credentials.
In pursuit of its mission to combat global cybercrime, Group-IB remains committed to sharing its Classiscam findings, sourced from their proprietary Digital Risk Protection solution, with law enforcement agencies. The primary objective of this research is to heighten public awareness regarding the latest scamming techniques and reduce the number of victims ensnared by this elaborate scam operation.
Global Expansion: From Russia to 79 Countries
Originally emerging in Russia, Classiscam underwent rigorous testing before being unleashed on a global scale. The affiliate program for this scam-as-a-service operation saw a surge in popularity in the spring of 2020, coinciding with the onset of COVID-19 and the subsequent increase in remote work and online shopping.
Group-IB experts observed the exportation of the scam scheme to Europe before infiltrating other global regions, including the United States, the Middle East and Africa (MEA), and the Asia-Pacific (APAC) region. As of 1H21, Classiscammers had targeted users in 30 countries. Remarkably, by 1H23, this number had soared to 79. During the same time frame, the count of targeted brands on the global stage rose from 38 to a staggering 251.
Regional Targets and Financial Impact
Analysis by Group-IB experts revealed that over 61% of Classiscam’s resources, created between 1H21 and 1H23, targeted users in Europe. The Middle East and Africa (MEA) accounted for 18.7% of targets, while the Asia-Pacific region (APAC) constituted 12.2%. Detailed statistics on the distribution of targeted brands by region can be found in Figure 2.
Within the APAC region, Australia was the most heavily targeted country, making up 34.6% of the regional total. Other prominent targets in the region included India (11.5%), Hong Kong (10.3%), Singapore (7.7%), Sri Lanka (7.7%), and Malaysia (5.1%).
Financial Toll on Victims
The average loss incurred by Classiscam victims worldwide stood at US$353, with UK users experiencing the highest average loss, amounting to US$865 per fraudulent transaction. In contrast, APAC and MEA users were less susceptible, although Singaporean victims, on average, lost US$682 to the scam. Australian victims faced an average loss of US$515, while Saudi Arabian victims (MEA) lost an average of US$525 to successful Classiscam schemes.
Evolving Tactics: From Simple Scams to Full Automation
Classiscam’s initial incarnation involved fraudulent advertisements on classified sites and the use of social engineering tactics to deceive users into making payments or disclosing their bank card information. Over the past two years, the operation has evolved significantly, now employing Telegram bots and chats for seamless coordination and the rapid creation of phishing and scam pages. These groups offer user-friendly instructions, and experts are on standby to assist with inquiries.
Role specialisation within scam groups has become more pronounced, with Classiscam phishing pages now featuring balance checks to assess the potential charge to a victim’s card and fake bank login pages to harvest credentials.
Group-IB experts have identified 35 such scam groups distributing links to phishing pages with fake login forms for banking services. In total, Classiscam scammers have replicated the login pages of 63 banks across 14 countries.
Continued Vigilance in the Face of Automation
Afiq Sasman, head of Group-IB’s Computer Emergency Response Team in the Asia Pacific, emphasised that “Classiscam shows no sign of slowing down, and the ranks of the Classiscammers are continuing to swell”.
He highlighted the adoption of an expanded hierarchy within scam groups and the growing specialization of roles. The scheme’s full automation and low technical entry barrier make it likely to persist as a major global scam operation throughout 2023.
Group-IB remains steadfast in its commitment to monitor global Classiscam campaigns and collaborate with law enforcement agencies and affected brands to dismantle these scams. Companies whose brand identities are impersonated by scammers are encouraged to leverage Digital Risk Protection solutions for proactive monitoring, identification, and takedown of phishing domains.