Sophos, a global cybersecurity leader, has recently released its 2024 Threat Report, focusing on ‘Cybercrime on Main Street’ and detailing significant threats facing SMEs.
In 2023, nearly half of malware detections targeting SMEs comprised keyloggers, spyware, and stealers—tools cyber adversaries use to pilfer valuable data and sensitive credentials, enabling unauthorised remote access, extortion, ransomware, and more.
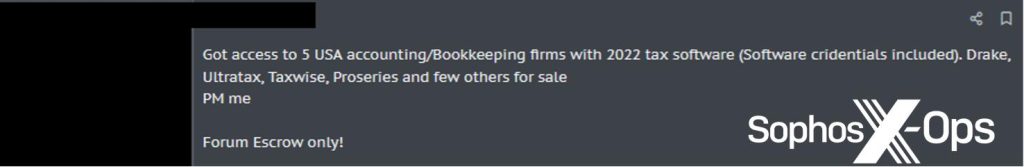
The report delves into the ominous realm of initial access brokers (IABs), cybercriminals specialising in infiltrating computer networks. IABs actively use the dark web to advertise their skills, either targeting specific SMB networks or selling pre-compromised access to those they have successfully breached.
A sample dark web forum post, uncovered by Sophos X-Ops, advertises access to a small US accounting firm. Additional instances of cybercriminal forum advertisements, categorized by industry and country, are compiled in the 2024 Threat Report.
Christopher Budd, director of Sophos X-Ops research, highlights the exponential surge in the perceived value of ‘data’ as a form of currency in the cyber underworld, particularly impacting SMEs.
Notably, the report underscores that over 90% of reported cyberattacks in 2023 involved data or credential theft, spanning ransomware attacks, data extortion, unauthorised remote access, and straightforward data theft.
While ransomware attacks against SMEs have stabilized in numbers, they persist as the predominant cyber threat. Sophos Incident Response (IR) interventions reveal LockBit as the foremost ransomware gang, closely trailed by Akira and BlackCat.
SMEs also face attacks from residual older and lesser-known ransomware variants, such as BitLocker and Crytox.
The report emphasises the dynamic evolution of ransomware tactics, marked by an increase in leveraging remote encryption and a strategic focus on targeting Managed Service Providers (MSPs). Notably, between 2022 and 2023, there was a substantial 62% surge in ransomware attacks involving remote encryption, indicative of a shifting threat landscape.
Adding complexity to the cybersecurity paradigm, Sophos’s Managed Detection and Response (MDR) team responded to five cases where small businesses fell victim to attacks orchestrated through vulnerabilities in their MSPs’ Remote Monitoring and Management (RMM) software.
Post-ransomware, Business Email Compromise (BEC) attacks emerged as the second-highest type of cyber threat in 2023, as per Sophos Incident Response (IR) data. These BEC attacks, alongside other social engineering campaigns, witnessed a notable uptick in sophistication.
Cyber adversaries now engage targets through a series of conversational emails or even direct phone calls, enhancing the complexity of their deceitful tactics.
The report draws attention to the elusive maneuvers employed by cyber adversaries seeking to evade traditional spam prevention tools. Attackers experiment with novel formats for their malicious content, such as embedding code within images or deploying malicious attachments within OneNote or archive formats.
An illustrative case detailed in the report describes attackers sending a PDF document featuring a deliberately blurry and unreadable thumbnail of an “invoice,” concealing a malevolent link leading to a malicious website.
For a comprehensive exploration of these emerging cyber threats targeting SMEs, readers are encouraged to peruse the detailed insights provided in the 2024 Sophos Threat Report: Cybercrime on Main Street, available on Sophos.com.